SCADA Honeynet
Honeynets are a useful research tool to better understand attacks and attackers, and a useful early attack warning tool for network owners. The SCADA Honeynet mimics many of the services from a popular PLC and better helps SCADA researchers understand potential risks of exposed control system devices.
History
The first SCADA Honeynet was released in March of 2004 by Matthew Franz and Venkat Pothamsetty of the Cisco Critical Infrastructure Assurance Group (CIAG). The design utilized Honeyd for simulating a limited set of services from a popular PLC. To date the project is not maintained, however is still available from Sourceforge.
Current
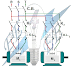
The current SCADA Honeynet managed by Digital Bond utilizes two virtual machines. One virtual machine concentrates on monitoring all network activity and statistics by utilizing a Generation III Honeywall. The Honeywall virtual machine image contains Digital Bond’s Quickdraw IDS signatures to detect any malicious attacks that may occur against the second virtual machine, a simulated PLC. The second virtual machine, the target, simulates a popular PLC that exposes a number of services to an attacker. The virtual machines images are available for download as the Digital Bond subscriber site.
SCADA Honeynet Download
The SCADA Honeynet and SCADA Honeywall are available to digitalbond.com site subscribers – - which is free of charge.
Modbus TCP
The SCADA Honeynet exposes the Modbus TCP protocol and contains a points list from a US Electric substation. Points represent measured values such as voltage and current and status such as a protective relay, like a circuit breaker, being open or tripped. An attacker with a easily available Modbus client could read the points and even write changes to the simulated PLC that would affect the integrity of a substation if the PLC was a real device.
FTP
The SCADA Honeynet exposes a VxWorks FTP service mimicking that of a real PLC. Banners, default logins and default passwords have all been duplicated to fool attackers into logging into the device. Since FTP is a clear text protocol all full content network communications are inspected by the Honeywall snort and [[SCADA IDS Signatures]].
Telnet
The Telnet service and banners are exposed on the SCADA Honeynet. No interaction is available, however a VxWorks login banner is presented and available to attackers.
HTTP
The popular PLC hosts a custom embedded HTTP server for easy device management. A open source web server is available to attackers and key components such as the content (images, java applets, etc) and HTTP server types have been duplicated.
SNMP
The SCADA Honeynet supports the full SNMP MIB of the mimicked PLC.
| Service | Port | Purpose |
| FTP | tcp/21 | Firmware/Device Management |
| Telnet | tcp/23 | Device Configuration/Management |
| HTTP | tcp/80 | Device Configuration/Management |
| SNMP | udp/161 | Device/Service Health/Statistics |
| Modbus TCP | tcp/502 | Monitoring and Control |
SCADA Honeywall
Honeynets are a useful research tool to better understand attacks and attackers, and a useful early attack warning tool for asset owners. Many asset owners requested the ability to replace the simulated PLC target with a physical field device of their own. Digital Bond’s SCADA Honeywall is a modified version of the SCADA Honeynet that can be placed in front of a real PLC or other control system device.
The SCADA Honeywall is based on the roo from the Honeynet Project and runs on Linux. The Honeywall is used to track and manage the attacker. It includes the Snort IDS in packet capture mode, and Digital Bond has added their SCADA IDS signatures. The SCADA Honeywall image also includes:
- Sebek – a white hat rootkit
- Argus – to collect network statistics
- Walleye – web-based management interface
- Mysql – store data
The SCADA Honeywall can create periodic activity reports or be configured to alarm when attacks are identified. Since there is no reason for any activity to pass through the SCADA Honeywall, any attack activity is likely to warrant immediate investigation.
Using a PLC or control system device commonly found on an asset owners control network as the Honeynet target provides a highly realistic look and feel. In addition to the realism of the device, the data obtained from an attack on a PLC monitored by the SCADA Honeywall would provide a more accurate representation of the attacker’s sophistication.










0 التعليقات:
إرسال تعليق